What Type Of Data Uses Pop Protocol?
Introduction to Types of Networking Protocols
A Network Protocol is a group of rules accompanied by the network. Network protocols volition be formalized requirements and plans composed of rules, procedures, and types that describe communication amid a couple of devices over the network. The protocol can be described as an approach to rules that enable a couple of entities of a communication program to transfer information through any type of variety of a physical medium. The protocol identifies the rules, syntax, semantics, and synchronization of communication and feasible error managing methods. In this article, we will discuss the different types of networking protocols.
Different Types of Networking Protocols
Below are the different types of Networking Protocols.
1. HTTP or HTTPs
- This stands for Hypertext Transfer Protocol or Hypertext Transfer Protocol (secure). The secure version is encrypted, meaning that nosotros will encrypt all the data as we ship it from the customer to the server.

Application Layer (7) HTTP HTTPS
Transport Layer (4) 80 443
- Now client and server hither get very important with application layer protocol. Nearly all awarding-layer protocols use this model, using i device on the client'due south network, the other device on the network existence the server.
- Now when we are using HTTP or HTTPS or a transfer a file. Transferring a file in the format of the hypertext. Hypertext is readable past a web browser. The client software you are probable very familiar with. This is either Google Chrome or Firefox, which may be Microsoft Edge or Apple's Safari browser. These are all web clients that support the utilise of HTTP or HTTPS.
- The server side too running some software. It's running server software. For the website, we commonly use Apache, which is open-source software that is a web server, which can run on either Linux or Windows. Nosotros take nginx, which is used in very big website deployments and tin can be run on UNIX. Nosotros have Microsoft'south Cyberspace Information Services or IIS, which tin be run on Microsoft systems. There are several web server options out that a server administrator can install to host a website on the net. So the whole purpose of the client-server hither is to have client software like a spider web browser and the web server like Apache work in conjunction with each other and transfer these hypertext documents to get the website from the server to the client.
- The Port number uniquely identifies the layer-7 protocol existence used at layer iv. We can use these port numbers to identify traffic at layer 4 easily, The HTTP by default, we have port 80, and for HTTPS by default, we have port 443 as the transport layer protocols.
2. FTP (File Transfer Protocol)
- The FTP allows usa to transfer files from a client to a server or from a server to a client.
- We tin do it in both directions here, and this protocol is either going to be FTP, sFTP, or TFTP.
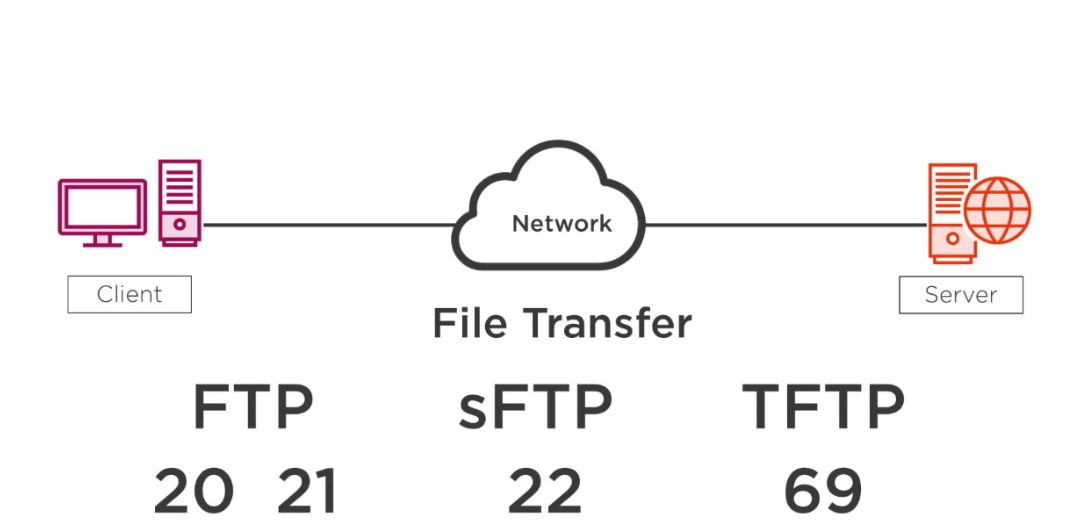
- FTP is a File Transfer Protocol, SFTP is a SecureFile Transfer Protocol, and TFTP is a Footling File Transfer Protocol.
- FTP and SFTP are pretty like to one another. These protocols will transfer files from ane device to the other, and in that location is client and server software specifically designed to do this.
- TFTP works a little chip differently. It's really meant for sending tiny files between two devices or having simple setups where you can transfer a file quickly without worrying about hallmark or having whatsoever issues with firewalls causing your traffic to be knocked downwards.
- FTP and SFTP typically require both a username and a password in order to transfer these files. TFTP does not crave this. SFTP specifically here is going to encrypt the traffic.
- FTP will use both ports xx and 21; ane is used for authentication; the other is used for transferring information. Port 22 is used for SFTP, and the reason for that is port 22 is actually the port number for another protocol nosotros are going to await at called Secure Shell or SSH, and what happens here is nosotros really take the FTP protocol, and nosotros put information technology inside of an SSH session, which allows usa to encrypt traffic and is why the port numbers are the same for both SFTP and SSH. TFTP uses port number 69.
3. E-mail Protocols (POP3, IMAP, SMTP)
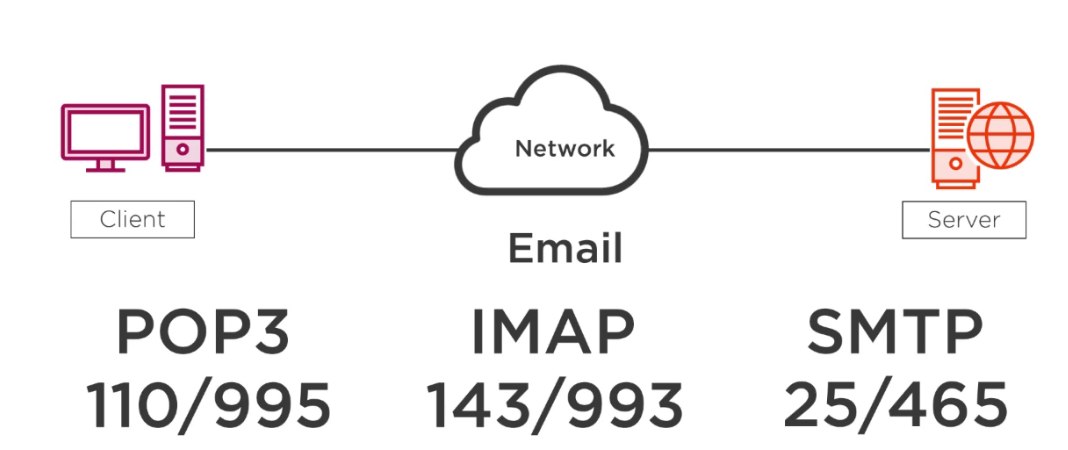
- Email is specifically designed for transferring files. We are transferring files that are actually in the format of these e-mail documents. For e-mail, nosotros have three protocols nosotros use. Two of them are used by a customer to retrieve mail from a server. So POP and IMAP are explicitly used to take email messages that live currently on a server, maybe Gmail or maybe your visitor's e-mail server, and they use it to transfer those email messages over to your client, some type of mail client that resides on your workstation.
- SMTP, still, is a Elementary Mail Transfer Protocol. This protocol takes a message that you create on a client email application, and it uses it then to ship that email to an SMTP server. SMTP is used to forward the email to the server; the server then figures out how to get letters to the recipient that y'all intended.
- POP stands for Post Office Protocol; we are using version 3 in that location.
- IMAP is Internet Message Access Protocol, so like SMTP is the Unproblematic Mail service Transfer Protocol. All these protocols work either in unencrypted or encrypted modes.
- And then here with POP3, for unencrypted traffic, we will use port 110; for encrypted traffic, we will use port 995. IMAP, we will use port 143 for the unencrypted traffic, port 993 for encrypted traffic, and for SMTP, we volition utilise port 25 for unencrypted and 465 for encrypted.
four. TCP(Transmission Control Protocol) and UDP(User Datagram Protocol)
In that location are two common network protocols used to ship information packets over a network. Together, TCP and UDP are alee of the data packets through your device, applying ports to different routers until they connect with the last destination. Also, they are utilized to send out the packets towards the IP accost with the receiver. Equally, TCP as well as UDP focus on the pinnacle of IP, or Internet Protocol.
TCP/IP
UDP/IP, which is used very frequently, but they are just referred to as TCP and UDP.
- TCP is amongst the most widely used protocol using the internet.
- TCP is a two-fashion chat.
- TCP is focused on stability.
- Packets will be instructed and numbered.
- Packets will exist error-checked.
UDP
UDP would not perform all of the fault-checking made past TCP
- Error checking slower points down.
- Packets are simply delivered to the recipient.
Utilized in one case speed is desired every bit well as, error modification will be required
- Live broadcasts
Conclusion
Although the older idea of the network is ordinarily foundational during almost all parts of civilization, Computer Networks and Protocols possess permanently transformed the manner human beings work, perform and connect. Forging strongly into parts of existence that nobody had predicted, digital networking is additional strengthening us in the future. New protocols and requirements will come out, new applications tin can exist developed, and our lifetimes will probably be additionally transformed and improved.
Recommended Articles
This has been a guide to Types of Networking Protocols. Here we hash out the basic concept and different types of protocols with a detail explanation. You can as well get through our other suggested articles to acquire more –
- Networking Devices
- Networking Strategies
- Computer Hardware vs Networking
- Networking Interview Questions
What Type Of Data Uses Pop Protocol?,
Source: https://www.educba.com/types-of-networking-protocols/
Posted by: grangerwhatedou.blogspot.com


0 Response to "What Type Of Data Uses Pop Protocol?"
Post a Comment